In today’s interconnected digital landscape, businesses increasingly rely on third-party vendors to enhance their services, optimize operations, and reduce costs. While these partnerships bring significant advantages, they also introduce new cybersecurity risks. A breach at any point in the supply chain can have devastating consequences, potentially exposing sensitive data or disrupting operations. This is where Third-Party Vendor Risk Management (TPRM) becomes essential.
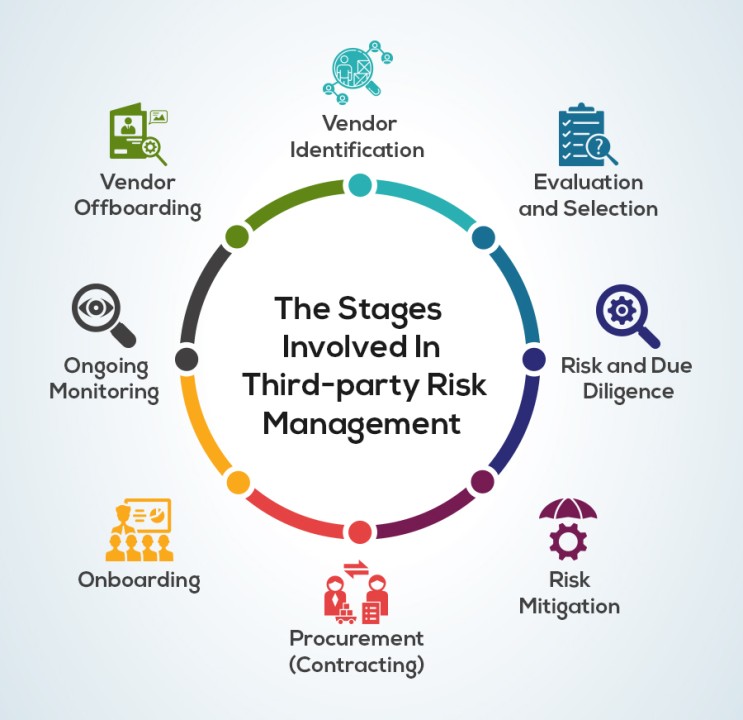
Why Third-Party Vendor Risk Management is Critical
Vendors often have direct or indirect access to your systems, data, and customers, making them a potential weak link in your cybersecurity defense. An attack on one vendor can create a domino effect, compromising multiple organizations.
High-profile breaches, such as the Target breach in 2013—where attackers gained access through a third-party HVAC vendor—demonstrate how third-party vulnerabilities can lead to significant financial and reputational damage.
Vendor risks can include:
- Data Breaches: If a vendor mishandles sensitive data or lacks strong security measures, it could expose your organization to breaches.
- Non-Compliance: If your vendors fail to comply with regulations (e.g., GDPR, PCI DSS), your business could be held accountable.
- Operational Disruptions: A cyberattack on a key vendor could disrupt your supply chain, affecting your ability to deliver products or services.
- Reputational Damage: If a vendor experiences a breach that affects your customers, your brand’s reputation may suffer, even if your systems were not directly compromised.
TPRM is designed to address these risks by ensuring that your third-party vendors adhere to robust security standards and minimize the potential for cybersecurity incidents.
Common Risks in the Supply Chain
Here are some of the most common risks associated with third-party vendors:
- Inadequate Security Practices
Vendors may not implement the same rigorous security controls that you do, leaving gaps that can be exploited by attackers. This includes weak password policies, lack of encryption, or outdated software. - Unsecured Data Sharing
Vendors may have access to your sensitive data for operational purposes. If this data is not properly secured or transmitted, it could be intercepted or stolen during transfer. - Insufficient Vendor Due Diligence
Failing to thoroughly vet third-party vendors before onboarding them can lead to partnerships with companies that have poor cybersecurity practices, exposing your business to unnecessary risk. - Complex Supply Chains
Some vendors may use their own third-party suppliers, creating a complex supply chain where the security of each entity impacts the others. This complicates risk management, as threats can originate from deeper within the supply chain. - Lack of Incident Response Coordination
In the event of a cyber incident, the lack of a coordinated response plan between your organization and the vendor can delay remediation efforts and escalate the impact.
Best Practices for Third-Party Vendor Risk Management
Securing your supply chain involves a structured approach to managing third-party risks. Below are some of the key best practices to follow:
1. Conduct Thorough Vendor Risk Assessments
Before engaging with any vendor, conduct a comprehensive risk assessment to evaluate their security practices and potential impact on your business. Key areas to evaluate include:
- Data protection policies
- Security certifications (e.g., ISO 27001, SOC 2)
- Compliance with industry regulations (GDPR, HIPAA, PCI DSS)
- History of cybersecurity incidents or breaches
This risk assessment should be a part of your vendor onboarding process to ensure that any new partnership aligns with your security requirements.
2. Establish Clear Security Requirements in Contracts
Your vendor contracts should include clear, enforceable security requirements. These should cover:
- Data protection and encryption standards
- Incident response protocols
- Regular security audits and assessments
- Compliance with industry regulations
Ensure that vendors are contractually obligated to maintain these security standards throughout the relationship, and define penalties for non-compliance.
3. Implement Continuous Monitoring
Vendor risk management is not a one-time task. Once a vendor is onboarded, continuous monitoring is crucial to track any changes in their security posture. Use security tools to monitor vendor activities, such as network traffic, and establish protocols for periodic reassessments of their security policies.
Tools like Security Ratings or Vendor Risk Management Platforms can help monitor a vendor’s risk in real-time, providing alerts when new vulnerabilities or incidents arise.
4. Limit Vendor Access to Critical Data
The principle of least privilege should be applied to vendors, meaning that they only have access to the data or systems they need to perform their functions. Segment your network to limit the risk of lateral movement if a vendor is compromised, and ensure that access to sensitive information is strictly controlled.
5. Establish Incident Response Collaboration
Develop a joint incident response plan with your vendors. Ensure that they have an effective breach notification process in place and that your teams can collaborate in the event of a cyber incident. This collaboration should include:
- Defined communication channels and escalation paths
- Specific roles and responsibilities for managing incidents
- Agreed-upon timeframes for reporting breaches (e.g., within 24 hours)
A quick, coordinated response can help mitigate the impact of a cyber incident involving a third-party vendor.
6. Audit and Review Vendors Regularly
Schedule regular security audits and reviews of your vendors to ensure ongoing compliance with your security policies. Use the audits to assess:
- Changes in the vendor’s security posture
- New risks or vulnerabilities that have emerged
- Updates to regulatory requirements
Regular reviews will help you stay ahead of potential risks and ensure that your vendors remain compliant with your security standards.
How to Build a Vendor Risk Management Program
Building a robust Vendor Risk Management (VRM) program is essential to securing your supply chain. Below are the key steps involved in establishing an effective VRM program:
- Identify and Classify Vendors
Start by identifying all third-party vendors and classifying them based on their level of access to sensitive data or critical systems. High-risk vendors—those with access to sensitive data or crucial business operations—should be given the highest level of scrutiny. - Develop a Vendor Risk Policy
Create a formal vendor risk policy that outlines the procedures for assessing and managing third-party risks. This should include a standardized process for vendor onboarding, monitoring, and termination. - Onboard Vendors with Security in Mind
Incorporate security into your vendor onboarding process by conducting risk assessments, reviewing security certifications, and ensuring that vendors agree to your security requirements before initiating partnerships. - Leverage Technology for Continuous Monitoring
Use vendor risk management platforms to continuously monitor vendor activities and receive real-time alerts about new vulnerabilities or incidents. Automation tools can help streamline this process and provide ongoing visibility into vendor risks. - Regularly Review and Update Your Program
Cyber risks are constantly evolving, and so should your VRM program. Regularly review and update your vendor risk management processes to align with new security threats, industry best practices, and regulatory requirements.
Conclusion
Third-party vendor risk management is crucial for safeguarding your business from cyber threats that can arise within your supply chain. By implementing strong risk assessments, continuous monitoring, and clear security policies, you can mitigate these risks and ensure that your partnerships with vendors do not compromise your organization’s cybersecurity.
Securing your supply chain is a long-term commitment, but with the right processes in place, you can greatly reduce the risk of a breach, protect your sensitive data, and maintain trust with your customers.












